Penetration Testing Malaysia: How to Hack-Proof your Network
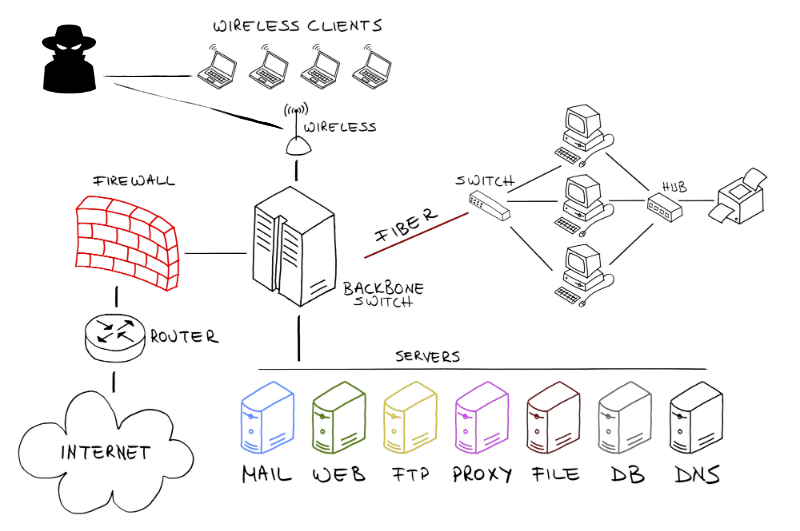
Unless you have been living under a rock, you are probably familiar with the words “cyber-attack”, “online fraud”, “cybercrime”. For an average person, this is just some techy term where there is a “loss” that has to do with sensitive information (such as bank details, network password, company data) leaking online.
For an individual, this might not mean much. But if you are running a business, then you better do something to protect your company data as well as your customers’ data safe from cyberattacks.
Pentest Company in Malaysia
A penetration testing company offers a comprehensive data analysis, strategical planning and secure network implementation to help a business secure their networks.
Finding a pentest company in Malaysia is a straightforward process. You can easily get a list of penetration test companies online. Some of the top pen test service providers also have a section where you can easily compare one pentester company to the other.
Do you Need Penetration Testing?
Since most if not all businesses do online transactions, may it be for selling products or uploading client data on the cloud, all need to do regular system checks and maintenance. This is where penetration testing comes in. Here is a list of penetration testing services that you should consider.
1. Mobile App Penetration Testing
Mobile application penetration testing is done before launching the mobile app and regularly thereafter during new releases. This keeps the application’s system up to date and safe to use. Click here to find out more information.

2. Wireless Network Penetration Malaysia
Whether you are a restaurant or a financial institution, securing your network is essential not only to protect your company from cyber attacks but to protect your customers as well who are enjoying your wireless network.
3. Web App Penetration Test Malaysia
Web application penetration testing is a process by which a pentest expert tries to hack into your web application to check for vulnerabilities. Keeping your web applications updated and secure is important to prevent data loss.
4. Source Code Review
Whether it is a website, a mobile app or a software application, it is important to have someone review the code. Unnecessary code can make your applications and your website vulnerable to hacks. A source code review is usually done before launching the app or website and should be done on a regular basis.
5. SWIFT Security Assessment Service
For banks and financial institutions who transfer billions of dollars daily, a SWIFT security assessment service is needed. The SWIFT Security Assessment Service logical and technical components, based on SWIFT Recommended guidelines.
This will include Business and IT process review, Physical and Logical Access Control Review, Network Monitoring Process Review, Security Incident Management Process Review, Internal Network Vulnerability Assessment and Penetration Testing, Host Configuration Review, Network Device Configuration Review, and Network Architecture Review.
Finding a Reliable Penetration Testing Company in Malaysia
Though you can easily get a list of penetration test companies online, finding a reliable pen test company can be a headache. Here are some tips that you can use.
Check and compare pen test companies according to the service that you need. Some pen test companies specialize in a certain area of security. Though they also handle other types of penetration testing, finding someone that specializes in giving you what your company needs would ideal.
Crest Pentest Malaysia
The crest is a nonprofit organization that sets standards and protocols as well as evaluate organizations who wish to offer penetration testing services. So, if you are looking for the best pen testing company, then look for a Crest Pentest Malaysia certification.
